Vulnerability Dashboard¶
Relevant Regulations¶
GDPR¶
Taking into account the state of the art [...] the controller and the processor shall implement [...] as appropriate [...] a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing.
In assessing the appropriate level of security account shall be taken in particular of the risks that are presented by processing, in particular from accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to personal data transmitted, stored or otherwise processed. [highlights added]
Swedish Patient Data Law¶
Note
This regulation is only available in Swedish. To avoid confusion, we decided not to produce an unofficial translation.
10 § Vårdgivaren ska vid utveckling, idrifttagande och ändring av informationssystem som används för behandling av personuppgifter säkerställa att personuppgifternas tillgänglighet, riktighet, konfidentialitet och spårbarhet inte riskeras.
Welkin Vulnerability Dashboard¶
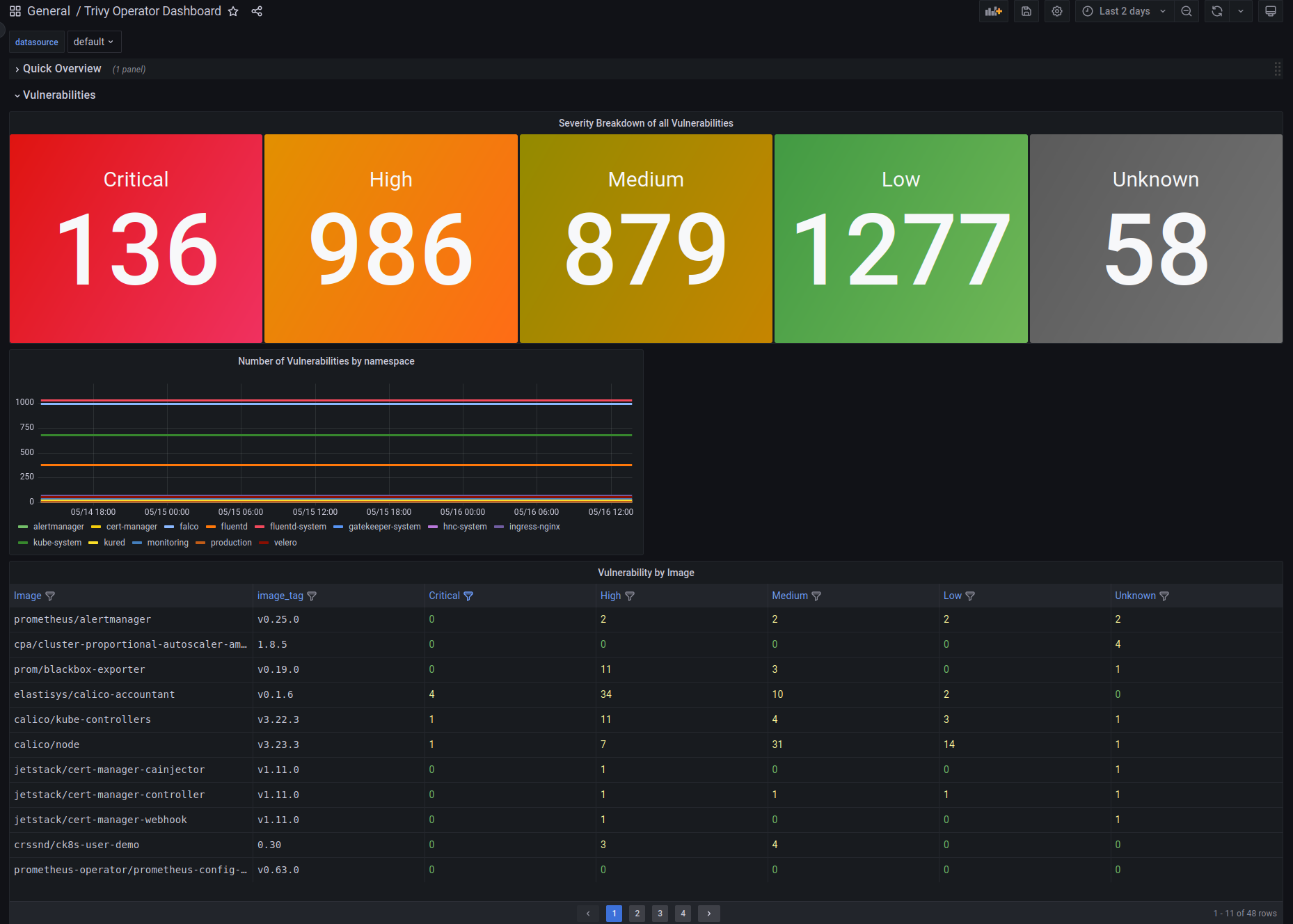
The Welkin Vulnerability Dashboard (Trivy Operator Dashboard) allows to audit what vulnerable container images are running in production. The dashboard allows to asses increase or decrease of exposure over time. It also allows to prioritize vulnerabilities based on CVE score (CVSS).
Therefore, this dashboard should be regularly reviewed, perhaps even daily. A vulnerability management process should be in place to decide how to systematically handle vulnerabilities.
Handling Non-Compliance¶
Containers should preferably be redeployed with an image that received the necessary security fixes. In case the security fix cannot be deployed in a timely manner -- e.g., due to a slow fix from the vendor -- then the affected containers should be terminated. In all cases, isolating a container using NetworkPolicies, non-root user accounts, no service account token, etc. can make a vulnerability more difficult to exploit.
